What are disadvantages of Let's Encrypt
Letsencrypt is now installed on more than 50% of all webservers. This is mostly thanks to its adoption by many web hosting providers. We can also see it starts being used by large companies and enterprises. But what are the downsides?
First of all - certificates' (including Let's Encrypt certificates) main task is to prove the authenticity of their owner, e.g., a web server. There is no difference between Let’s Encrypt and any other certificate your browser can verify (DigiCert, COMODO, Entrust, etc), and all browsers can now verify Let’s Encrypt certificates.
Rate Limits
When we look at limitations of Let's Encrypt, they are mostly operational. There is one big disadvantage of Let’s Encrypt - rate limits. These restrict the number of operations you can do per second, hour, week, depending on the type of requests. The limits are most severe for the number of certificates you can issue per “registered domain”, e.g. keychest.net. I have described most of those limits here.
New management approach
Further, when using a Let’s Encrypt certificate, there are significant operational differences, i.e., how you manage such a certificate on your server.
Let’s Encrypt uses a set of new protocols for automated certificate management. There are two important effects of that:
- The process of issuing a certificate is different from most other CAs, which require manual steps, notably proving that you are the owner of a given server.
- The same process is designed to work fully automatically. Let’s Encrypt is about automation to keep the certificate issuance costs low. There’s always a question how much you need to automate something you do once a year or maybe once every two years, this may be one of the reasons why Let’s Encrypt certificates are valid only 90 days.
As a result, you have to renew your certificates four times, but more likely 6 times a year (due to time overlap), but you can automate it, if you have the skills and/or support. I would also recommend monitoring that your automation works. (I have been active in this area so you can try our service KeyChest, which is free for 500 domains and personal use.)
Reliability (2017)
I have also recently looked into the reliability of Let’s Encrypt certificate issuance and described some of the results in my blog Let’s Encrypt uptime is 99.9% — or 98.8% without defects in 2017. It’s actually quite good for a completely new system, but much worse than commercial CAs. I came up with 2 numbers: 98.0% and 99.9%, and the real truth is somewhere between them for vast majority of users. 99.9% is when Let’s Encrypt was up for at least some of its users, 98.0% when it worked flawlessly.
Reliability (2019)
I have recently revisited the reliability of Let's Encrypt with data covering December 2018 to November 2019. I received an interesting reaction at the LE community forum. The initial response was that I have over-reported downtimes but my results were eventually accepted (after some double-checking).
The bottom line is that it hasn’t got much better over the last two years. Despite the total number of disruptions being lower and planned upgrades becoming a routine business-as-usual operation.
The most important figures - the uptime are similar to 2017.
- Uptime with full disruptions only: 2019 - 99.92%, 2017 - 99.86%
- Uptime when partial disruptions added: 2019 - 96.4%, 2017 - 98%
The 2019 operation includes two short disruptions (< 10 mins) of their OCSP service, which has immediate impact when users visit new web servers as the certificate validity can’ be confirmed.
Practical / operational consideration
From operational point of view, there is a number of differences from commercial certificates that may or may not be important.
The type of certificates
Till recently, I would say this is not too important as all types are accepted by web browsers. However, with the adoption of DNS CAA checks and notifications, the "more expensive" certificates can provide a better protection of certificate buyers.
- Let’s Encrypt offers only certificates with the lowest level of validations as this can be automated. These are called Domain Validated SSL Certificate.
- Other Certificate Authorities offer certificates with more through validation: organization validation (OV), or Extended Validation (EV). These verify requests for certificates more thoroughly
Validity of certificates
- Let’s Encrypt allows only 90 days validate where you need to reissue a certificate on every 90 days period.
- Other Certificate Authorities offers 1 to 3 years validity period for any type of certificate.
Missing CRL in Let's Encrypt certificates
- Let's Encrypt doesn't have certificate revocation lists (CRLs). It only offers real-time validation of certificates with the OCSP protocol.
- Other Certificate Authorities implement CRLs, which makes validation of certificates more reliable. I.e., short downtimes of Let's Encrypt OCSP servers mentioned in the uptime analysis would mean that Let's Encrypt websites can't be access during those periods.
Service for Certificates
- Let's Encrypt doesn't offer any service that would help you manage your certificates and their expiry.
- Other Certificate Authorities offer a range of services to improve overall security of your websites but also to manage your certificates.
Note: This is something where KeyChest significantly helps to establish level playing field for Let's Encrypt.
Phishing Problem
This is more a problem of a perception and expectations. SSL certificates are not a silver bullet solution. It only provides a particular function, i.e., encryption of traffic between your browser and a web server.
Let’s Encrypt has naturally become a go-to CA for phishers as it fully automates the issuance process and doesn't ask any questions.. Let’s Encrypt also argues that it is not its job to stop malicious sites from using its certificates. While it is factually correct, it goes against expectations that many people have. Expectations that helped Let's Encrypt become successful and expectations that lead to a massive increase of the HTTPS use.
This meant that phishers and malware distributors were free to use Let’s Encrypt without any risk of being banned or having their certificate revoked & one of the prominent example is that over 14,000 SSL Certificates issued to PayPal phishing sites.
"Color" of padlock
As a side note, and another aspect of the point 1 above. There is a special type of certificates - so called Extended Validation certificates, or EV certificates. When a server presents an EV certificate, browsers tend to show the company name, rather than a web address. You can see the difference below - a Let’s Encrypt certificate (top) and an EV certificate (bottom).

Domain validated certificate will only show the domain name.
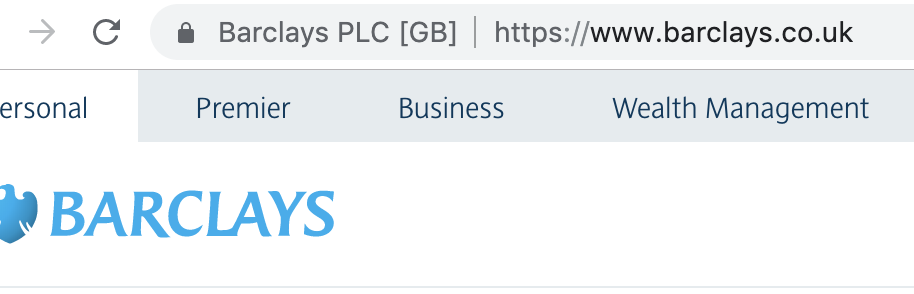
Extended validation (EV) certificate will show the company name.
