What does Let's Encrypt sell? It's not certs.
Last week saw huge coverage and celebration of Let's Encrypt, a free certificate authority that issued its billionth free certificate on Feb 27. But "if you are not paying for it, you're not the customer" ... are you the product being sold?
This is a quote from the official Let's Encrypt announcement:
One thing that’s different now is that the Web is much more encrypted than it was. In June of 2017, approximately 58% of page loads used HTTPS globally, 64% in the United States. Today 81% of page loads use HTTPS globally, and we’re at 91% in the United States! This is an incredible achievement. That’s a lot more privacy and security for everybody.
Let's Encrypt now protects almost 200 million domain names. As there are around 360 million registered domain names, Let's Encrypt has become a monopoly for HTTPS, with its certificates installed on more than 60% of all internet websites. As it is a not-for-profit organization, very few ask the question of its business model.
Who Is Let's Encrypt
Let's Encrypt is controlled by ISRG aka "A better internet". An organization founded by Mozilla, EFF (Electronic Frontier Foundation), the University of Michigan, Cisco, and Akamai. Its budget is today made up of donations from a large number of sponsors but 40% of all the funding comes from "platinum and gold level sponsors" - a much smaller group that consists of Mozilla, CISCO, OVHcloud, EFF, Chrome, Facebook, and Internet Society, IdenTrust, and The Ford Foundation.
These top sponsors also control the board of directors as well as the technical advisory board. The time and travel costs of the board members will be paid for from the internal budgets of their employers.
As much as I believe in charitable causes, no company gives money for nothing - there is always some kind of return on investment. It could be improving the brand value, but I haven't come across adverts that would say "proudly funding Let's Encrypt". Some want to use certificates for free - but really, only OVH does so. Google has its own CAs, CISCO doesn't really need them, Mozilla either and its website is Digicert protected, just like Facebook.
Let's have a look at another name from this list of companies - Akamai. Akamai is one of the largest CDN providers. If you think about what CDN does, you start wondering about the role of HTTPS. HTTPS is end-to-end encryption so if I encrypt end-to-end connections to my bank, how can Akamai cache and speed-up delivery of the bank's website across the globe? The answer is simple - Akamai is man-in-the-middle. It decrypts the bank website data and sends its copy of the data pretending to be the bank. The trouble is that to provide this speed and global coverage, Akamai needs to have private HTTPS keys of all its customers (e.g. the bank in this example) readily available. The way they do it is to keep all the private keys in plaintext files that are copied wherever they are needed. CDN providers represent 15-30% of internet traffic, which means that up to 30% of end-to-end encryption is not quite end-to-end.
What does HTTPS actually do?
When I worked for the University of Cambridge as a researcher, the security of the Internet was a frequent topic. I don't recall significant calls for "let's encrypt the whole of the internet". The debates were more around the effects of HTTPS. Do people notice anything like the color of the address bar (or even whether there's a small padlock) - frankly no one cares even today. Any such discussion today is obsolete as all cybercriminals have learned how to use and exploit HTTPS.
"Let's encrypt the whole of the internet" has some good justification but that was not enough to "sell the idea". There is a lot of misconception around what HTTPS can do. It's a little bit like "blockchain" that can allegedly solve almost all the problems of the world.
Let's try an example - we need HTTPS for secure use of APIs and embedding of third-party content on websites. So if I have my own company website: https://keychest.net, I can add a payment button - let's say Stripe - securely. Indeed, browsers will not allow the use of insecure HTTP from HTTPS websites - great. However, as any criminal can create an HTTPS service the added value is close to zero - encryption didn't solve the problem, we need something else! So how did we solve this "secure embedding" problem? Web servers can now provide a list of domains that can be embedded in their websites (content security policy - CSP). Nothing to do with HTTPS or encryption. It is a simple access control mechanism.
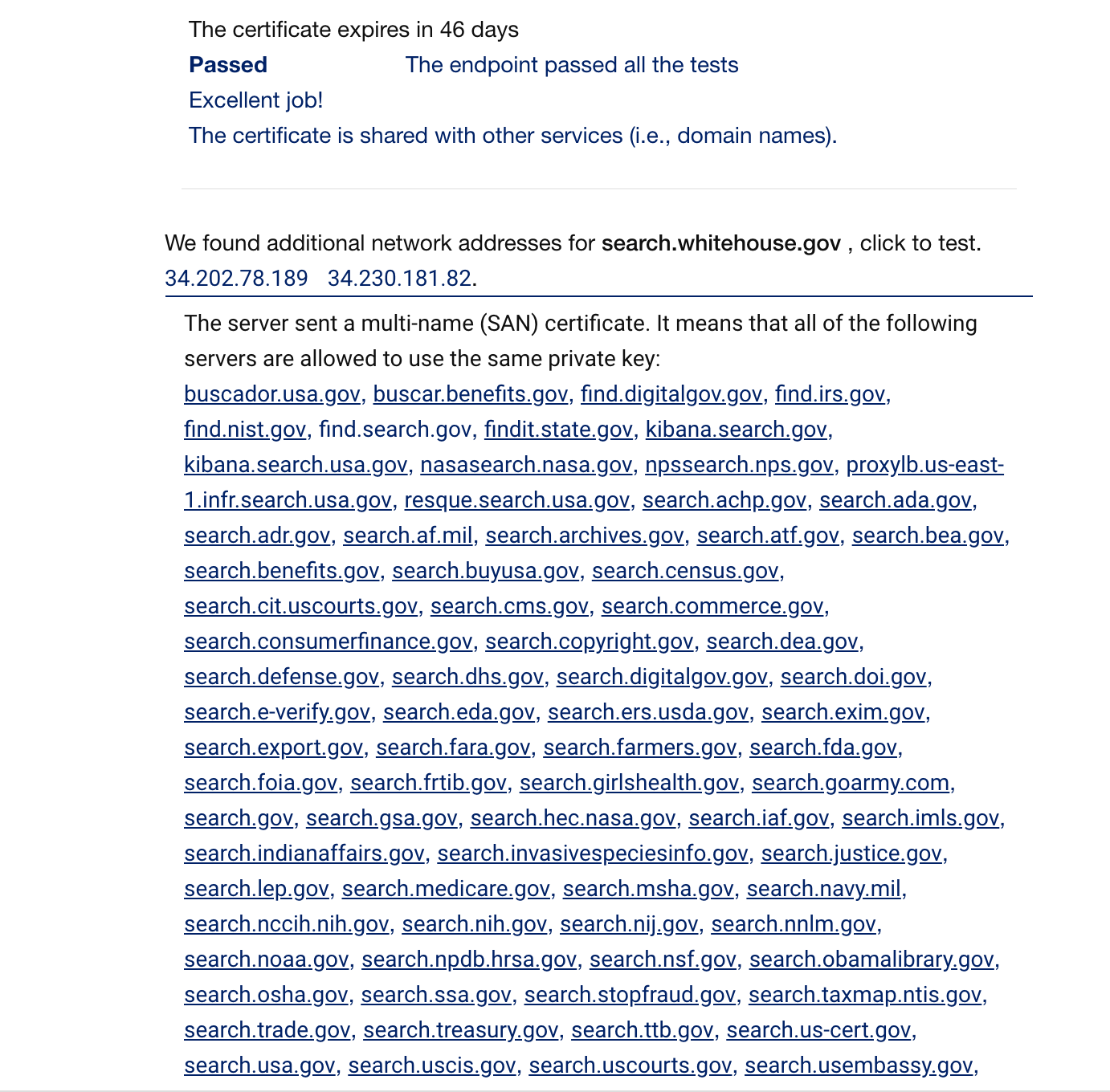
A single Let's Encrypt certificate
The other day, I put a question to the sysadmin subreddit. I basically said that HTTPS was a universal pain for small companies while it was really useful only in particular situations, such as when we need to exchange data items that are sensitive: credit card numbers, personal data, work documents, etc. I was "told off", of course. It was interesting, however, what examples were given to justify the HTTPS. They all involved big internet companies.
I mentioned the payment data as one of the most sensitive data that needs protection. Interestingly, anyone who processes payments is subject to PCI standards - something completely unrelated to HTTPS. PCI data processing requirements are pretty strict, mandate regular penetration testing by certified vendors and include pretty harsh penalties as well. As such, the global enforcement of HTTPS does not really have much of an impact on the security of this data.
I'm not saying that HTTPS is a bad idea, what I am saying is that it empowers a few companies that control our access to the internet through their web browsers and it's not quite clear to me whether this authority is justified.
Check the status of your web domain with our instant online domain audit tool.
What or Who Is The Product?
Just to remind you - the product of the two of the biggest sponsors of Let's Encrypt is our user data. So one could stretch the argument and say that they use HTTPS to strengthen their exclusive access to our personal and behavioral data. But maybe the exploitation of the HTTPS could go even further. Chris Matyszczyk wrote a post for ZDNet "Google says Microsoft Edge isn't secure. I asked Google why". The core argument of this article is that Google warns users that using non-Google add-ons or applications is not secure. I don't think it makes much difference to many a user but the impact is different if you are a company building those applications. How much risk related to a browser warning your users about the security are you willing to take. Is the cost of using a particular certificate / app store too high? You can get what the answer would be.
In a sense, HTTPS and security in general start being exploited for a wide range of commercial advantages. I wonder what is the place of Let's Encrypt in these online wars. I don't know the answer but I'm sure it's a long-term strategy game and only time will show.
Do We Need - Encrypt The Whole Internet?
It's interesting that mandatory HTTPS only really started once Let's Encrypt was up and running. As if Google and others were not so sure until people had to pay for certificates. Once Let's Encrypt was here, they thought it's fair to ask everyone to use HTTPS as certificates were "free". They are not really free - a hidden annual cost of a certificate is at least $40. If you're a geek at home with plenty of free "free" time on your hands you will disagree. For companies it is different - the cost is significant in their IT security budget. On top of that, any incident due to expired HTTPS costs revenue, real money. You can see a recent study of AppViewX, which we analyzed here, which confirms an earlier study of Venafi - 80% of companies experienced a related business outage.
One significant impact I noticed with Google implementing HTTPS (2010) on their server was the loss of search details for my websites. You can now find this via Google tools but it's only available with 1-2 days delay. One might say that HTTPS allows Google to determine who's the real owner of this data.
Not very many remember but the main Google argument against HTTPS was its cost. "Google says it’s been working for several months on the service, and that it’s not simple". We talking about the company that was worth around $200 million then. In short, web giants must be aware of the cost that HTTPS puts on small companies and yet, one has to notice the lack of justification. HTTPS is given credit for a lot of things it simply does not do and many keep quiet about problems it introduced. The Hacker News just published an article that says:
Capping certificate lifetimes improves website security, not least because it reduces the possibility of criminals stealing neglected certificates to mount phishing and malware attacks.
Well - a typical phishing attack lasts hours or single days. That means that the phishers can even get a refund for their certificates as most providers give you a "one-month money-back guarantee"!
Is there a downside to a monopoly created by a not-for-profit company? When you try to find economic studies there are not many relevant to the situation of Let's Encrypt. Firstly - the market of HTTPS certificates is a commodity market - hugely competitive with a large number of vendors working with small margins … but only if you buy in bulk. For example, one certificate can cost you $50 if you buy one and <$1 if you buy 10,000 of them.
Can We Break Let's Encrypt Dominance?
It is hard, like really hard. The main reasons are business reasons. ISRG decided to completely disrupt the certificate market. While Let's Encrypt says its annual budget is just over $3.3 million, it took around 5 years to its first certificate. The time is mostly down to regulatory hoops. It's harder and longer than creating a new bank!
By disrupting the market, ISRG created a monopoly that is here to stay. Creating a new root certificate authority is expensive and takes 3-5 years. Who would be willing to invest into a 5-year project to compete with Let's Encrypt when the "product" is free?
Right, so we have an excellent source of certificates, right? Well, if it's so good, why are none (ok, there's one exception - OVH) of the main sponsors using Let's Encrypt? On top of that, I have started hearing about cases where Google doesn't trust Let's Encrypt certificates - why would they do it? Is the budget and activities of Chromium really completely independent of the group providing G-suite?
Having said that, Let's Encrypt is a bit tricky to use for companies. Let's Encrypt's justification of a short certificate life-cycle is not that persuasive and its main line is "automation allows us to shorten the validity and it makes the misuse of certificates harder" - an argument I queried above. The risk of expirations is simply too high and there are also additional technical constraints. Although these can be relaxed on request.
The bottom line is that we now have a monopoly for HTTPS that is not-for-profit but sponsored by big internet players. As such, it is difficult for me to get a clarity in terms of the real purpose of Let's Encrypt. As a result, I see the use of Let's Encrypt as a higher risk than using other commercial certificates. Especially if we can provide the latter for $5-6/yr.
I have written a post about the disadvantages of Let's Encrypt. I suppose the business risk of using a product of such a dominant vendor that doesn't have a clear business justification is good enough to be added to the list.
You’ve got better things to do than worry about web certificates. KeyChest is a certificate expiry management service with instant discovery of internet certificates - no software installation needed.

