C-level Cyber Security Report with Surprises
Thales regularly publishes a Data Threat Report. It is created from responses provided by high-level execs so one wouldn't expect to find anything much of interest. But I was wrong, this time.
The 2019 Data Threat Report by Thales is available online and you can download in exchange for your email from https://www.thalesesecurity.com/) or directly from their file server as a PDF. It is a high-level threat intelligence report collected from C-level execs from around the world. I didn't expect too many surprises, but there are several things that are worth mentioning.
This Is What I Expected
My first impression was that of a general inconclusiveness of many of the report's sections. Most charts are based on multi-choice questions with very little difference between the least likely and most likely. Let's take concerns around using Infrastructure as a Service (IaaS). The question has 9 options with the most concerning on 47% and least concerning on 42%. I am not sure what can this section of the report say except that IaaS has a number of significant issues - from SLA and liability for data encryption incidents. At the same time, all the questioned organizations use at least one instance of IaaS so clearly security concerns are outweighed by the perceived cost saving on managing own private cloud / data centers.
Unexpected In Expected - Low Use of FDE
Another example is a part about data security technologies. The most common is "file encryption" on 53% with the "data loss prevention" at the opposite end with 43% (if we ignore payment-specific items). Now, I believe it is impossible to use Windows without disk encryption inside an organization's domain. When we look at major public cloud platforms, they all integrate disk encryption in such a way that it's for me hard to imagine a corporation that wouldn't do it. Still, the survey shows that only 46% of companies use full-disk encryption. Is it because C-level execs don't know or because it is being used without an enterprise-wide project, or is it real?
Surprise 1 - EU Execs Are Relaxed About Cybersecurity
There are, however, two specific aspects of the survey that surprised me. The first one is how European companies are relaxed about cloud security. This question had topics that included failure of the provider, attacks on the cloud platform, compliance, key management, privacy. Across all those questions, only 35% of European respondents were concerned compared to the 45% of the global respondents.

That is a massive difference and quite surprising. If only for the fact that we have a fresh data protection regulation (GDPR) that allows penalties up to 4% of global turnover. It just can't be true, or can it.
Surprise 2 - Proliferation of Blockchain
The second massive surprise for me was that more than 30% of companies are worried about sensitive / regulated data being submitted to public ledgers and compromise of cryptocurrency. I find this somewhat surprising as pushing sensitive data is much harder than posting it to social networks. The responses suggest that 30% of companies use bitcoin or other public ledgers, which sounds like a high number to me, given the regulatory issues around using cryptocurrencies in business.

Another explanation could be that senior execs don't understand the technology and simply accept related risks as relevant til they are properly identified and assessed. Alternatively, they simply answered the survey and marked threats (e.g., compromise of exchange provider or redirecting cryptocurrency destination) they see as relevant regardless of whether they actually have any possible impact on their business. Still, a possibility of such a large number of companies to actively use cryptocurrencies is surprising.
Surprise 3 - IoT Security by Design May Actually Be Really Broken
My last note is about the security of the IoT (internet or insecurity of things - depends on where you stand). Interestingly, the level of security concerns is lower than it is with using public clouds. On average, less than 30% of companies worry about the data security there. I found quite interesting that the most concerning are attacks on low-cost devices:
- attacks on IoT devices will impact critical operations (33%);
- lack of frameworks and control;
- loss or theft of IoT devices;
- privacy violations (30%);
- discovery of sensitive data created by IoT devices;
- and so on
I was not sure how good is my empirical experience in my previous post where I talked about a likely failure of the "security by design". My premise there is that we focus on securing low-cost devices that are used to protect and manage high-value assets. I believe this will not work from the economic point of view. And here we go, the biggest concern among large companies is the impact of $5 a piece devices on "critical operations".
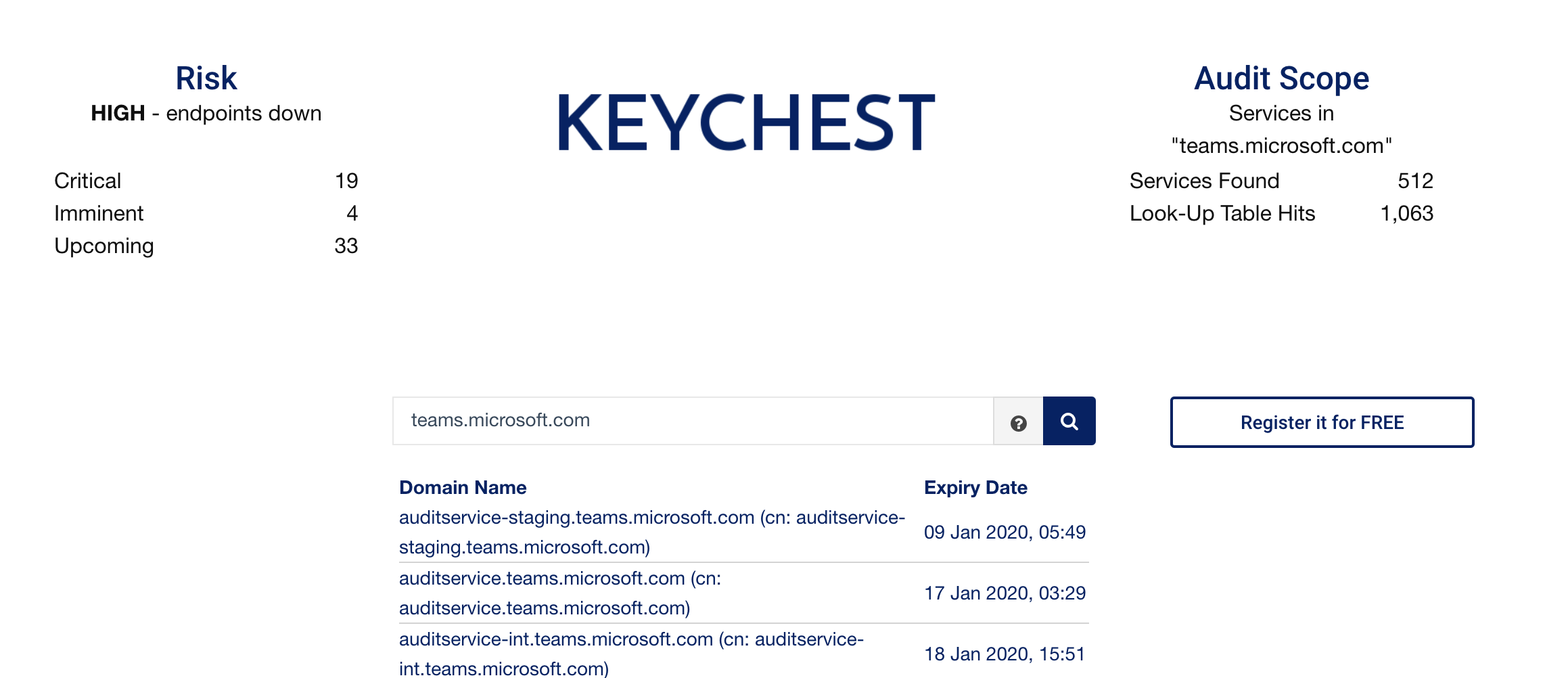
Instant audit of the teams.microsoft.com domain that experienced downtime due to an authorization certificate.
As the key management in the IoT world is currently almost a synonym of the "IoT security", we can only start managing cyber threats when we can create an accurate picture of whole IoT deployments. Once we know what the status is, we can start enforcing the baseline security policies and gradually improve the overall resilience against cyber attacks.
KeyChest with its global database of PKI certificates can instantly create an initial "big picture" so you can start analyzing your exposure to cyber attacks and adjust it according to your risk appetite.
