Secure By Design Will Not Work - The economics, stupid
Secure by design has been touted by governments as the way to solve the threat from insecure IoT devices. Here is a thought - it will never work because the focus is wrong.
The UK government has made "security by design" one of a handful of priorities in cyber-security. And they have claimed a significant progress admired across the globe. In October 2019, ARM, the processor design company, has announced a $50 million project to design a secure processor. A processor that is unlikely to ever go into production. The justification was "The government wants the UK to be the safest place to be online and the best place to start and grow a digital business"
The Economics In IoT
Here's why it will never scale-up to solve the problem of insecure IoT devices - the economics. IoT is the technology to manage high-value global assets, but IoT devices could cost less than $5 a piece in sales price. As far as I can see, the money for the security is on the user side, rather than IoT device manufacturers operating with much smaller margins.
Also, I am still to meet someone who is truly worried about the cybersecurity in the IoT world - I mean a user, not a vendor. There are many vendors writing about the importance of security in IoT. When you look at the "buyer" side, these voices are much harder to find.
Internet of Things - (source: Open Educational Resource - OER)
I had many discussions about IoT use cases and those with sensitive data are small and hardly scalable enough to make a vendor business plan viable for equity funding, i.e., likely to scale. IoT simply doesn't cater for sensitive data that would justify a proper security design, key management, and well, stop black hats laughing.
You can argue that key management - PKI - is fundamental for IoT. Yes, it is, but not necessarily for security reasons. What you need in an IoT network is to be able to identify devices and when you look at technology options, PKI as something fairly universal that can do the job. That's why you can find some kind of digital certificates in many devices. That's also why these default certificates are never updated or renewed.
Securing IoT Devices
There are initial drafts of standards - Software Updates for Internet of Things (SUIT) - https://datatracker.ietf.org/group/suit/about/ - that focus on the device security. To be more accurate, just and only secure updates. When I read the documents, my overall impression was that of a lot of technical details replicating secure boot principles from mobile devices. I did not find anything about how it should work in a wider IT ecosystem. For example, how would a secure upgrade work when device vendors are cut off from access to devices. Today, companies will not allow pushing OS upgrades into their networks without first testing them with their laptop/server images.
What are the chances of these standards having an impact that would scale globally? Not very good in my opinion as they go deep into the software stack of IoT devices, possibly all the way to the CPU level. It means an incredibly high cost of designing changes, implementing and testing. At the same time, it is not clear if IoT users have bought into this. It is much more likely that there will be "secure" versions of IoT products that would cost 5-10x more than "common" devices.
There is also a question of trust - who should hold the keys needed for firmware upgrades - these seem to be prone to leaks. We are talking about low-cost devices potentially protecting high-value assets. But the value is different for the IoT device manufacturer (low value) and the IoT device users (impact on high-value assets). In this respect, the SUIT documents may be getting assumptions for their architecture wrong. You can legislate but if there's no/weak business justification for proper security management, it may be seen as too heavy a price.
IoT Security = PKI, Not Really
It's possible you've never heard of "PKI" but it's a concept behind HTTPS - i.e., web encryption we all use now. It has become a commercial technology during the dotcom boom. At the time it had no practical applications. There was simply no viable use case. This has been a problem for a long time and it only has changed with an HTTPS proliferation in the last 5 years.
However, as IoT has become a buzzword for venture capital as one of the "future technologies", PKI has been rebranded as IoT security. And IoT security has been reduced to PKI. The trouble is that the PKI technology is incredibly complex and IoT devices are not able to implement it reliably.
PKI in IoT has to be significantly simplified to have a desirable security impact. We need to move as much functionality from devices to management systems to build the confidence in the IoT security required by businesses. Systems like KeyChest replace the focus on endpoints with a focus on the ecosystem to create and enforce a baseline security preventing attacks exploding weakest links.
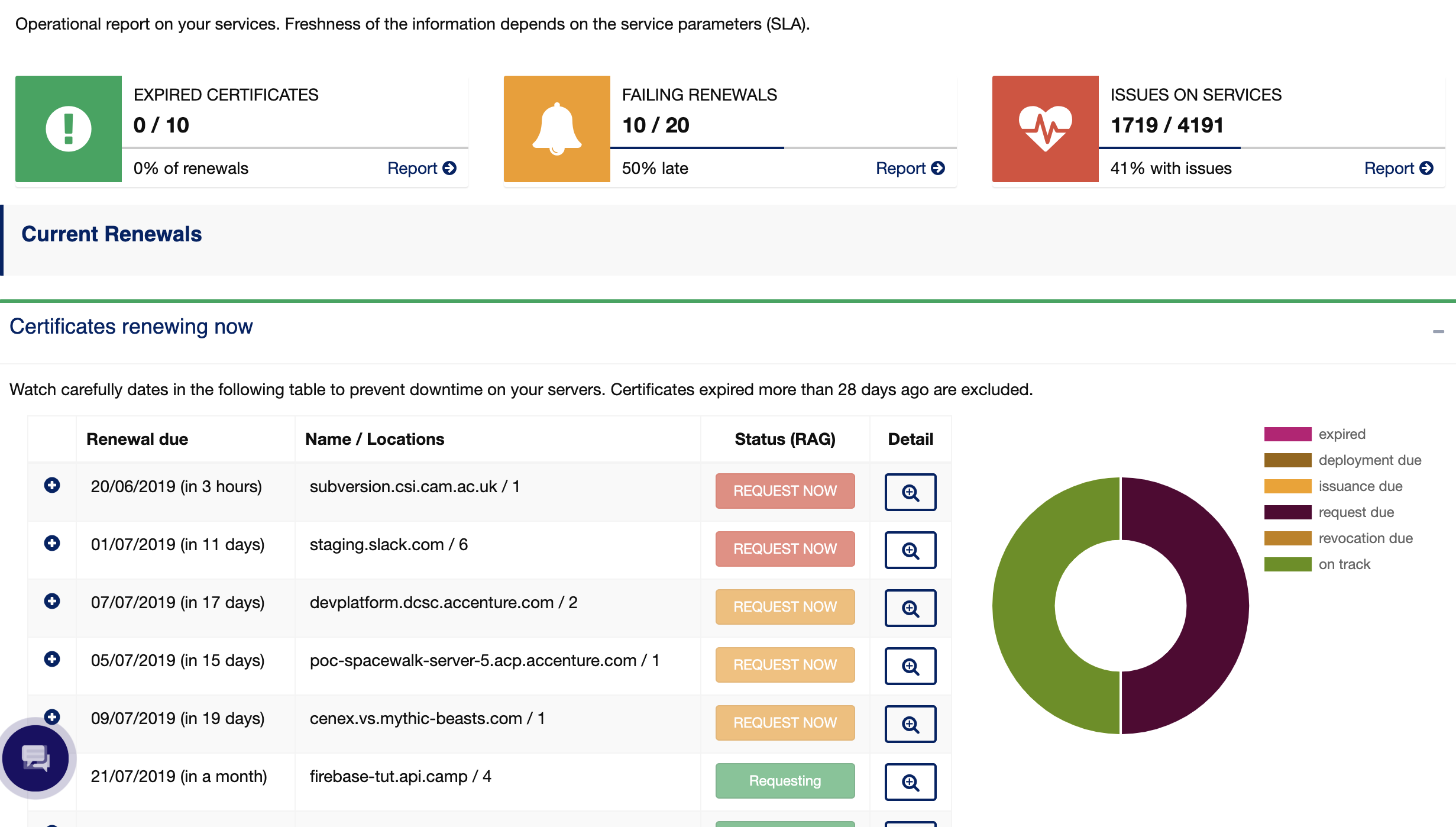
KeyChest provides a big picture of PKI status with its global database.
Despite all that, PKI is probably our best bet to implement a reliable device identification system and to bootstrap secure data transfers. We also need to move the difficult tasks from endpoints to high-security, possibly distributed, management systems. Recent research shows that the entropy of encryption keys generated by IoT devices is as little as 16 bits - remember that the minimum length for secure encryption is 128bits.
Key generation on devices should be limited to initial communication keys with their management systems. Simplify PKI operations to a core set that is absolutely necessary for any secure communication.
Encryption Fit for IoT = Simplicity
The Achille's heel of PKI is expiry. The first thing you can do is to "ignore" key/cert expiry. What I mean is that you replace "system breaking expiry" with business-managed expiry. IoT devices today suffer from a complete compromise of their security when their certificates expire. What you can do is to align the validity of certificates with the expected lifetime of IoT devices. You can then start managing risks from the business point of view and focus on the important aspects - incidents.
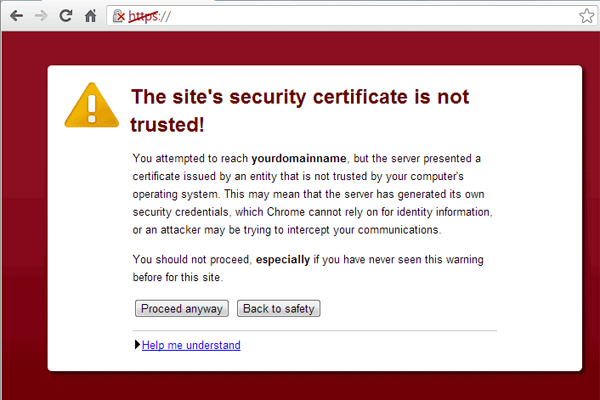
Expired certificates in IoT can cause downtimes, or a complete breakdown of encryption when security checks are bypassed.
It is absolutely incredible from the business point of view that a certificate that is perfectly secure at 11:59:59 is deemed useless, insecure, worthless at 12:00:00.
To simplify the encryption, my starting point would be that IoT is a mesh of devices that have a very small intersection of capabilities (much smaller than Windows, Android, iOS, ... have). In terms of the PKI, what you end up with is a signature on a name-key relationship. I would also assume that reliability is the primary concern, so you want to offload as much as you can from nodes to a management system - another reason to simplify certificates ... and another one is the size of certificates. (Did you know that the size of certificates breaks the binary encoding of TLS packets? They are just too long.)
For IoT devices, what we need are simple certificates with length limits on names to prevent memory issues. You also need a simplified chain validation algorithm. We want certificates to bootstrap trust not to define it. We can remove the risk of a root key compromise by deleting private key as soon as a batch of devices is personalized - whether it's done by the device vendor or a device user. You also need to create flexible, easy-to-recover mechanisms to validate root keys/certs - simplify incident recovery. Hacking these doesn't compromise root keys as they have been deleted long time ago => attacks can be fully contained with zero residual risk.
Inventory of IoT
A concept I really like is to mirror an IoT network with keys/certs just for the management purposes as it replaces a complex, heterogeneous system with an abstract inventory of keys that you can adjust to fit your management requirements. This can be a completely parallel inventory of what is actually installed on devices, or it can be tightly linked/identical with what is installed on devices. The expiry can then be used for an efficient management of data/device life-cycle.
The main questions still remain though - incident response. How do I expel a device from my network, how do I rollover issuing/root CA. Expelling devices is an issue only if you allow IoT devices to directly communicate with each other. If you have the internet access, you can as well proxy all traffic via an IoT management system. This way you can whitelist and/or blacklist devices. Direct communication between devices could use whitelisting, i.e., trust on first sight with blacklisting provided by the management system. While the direct trust can technically work here, it's still not clear if it makes the management way too complicated.
Encryption Is Not Security
Let me finish off with the main point. The IoT security is not defined by the strength of the encryption. It was said before that if you think the encryption can solve your problems, you don't know what your problems are. While working for Deloitte I was gobsmacked when I joined a discussion where the topic was whether an enterprise can achieve more than 90% data accuracy. It just completely changed the way I looked at the security of business applications.
There are use cases when each piece of data is important - like payment instructions from your credit card to your bank. But these are transactional data and we still need dispute resolution mechanisms and being able to identify fraudulent transactions and reverse them. When you look at business data in general, you create meaningful information from millions of data items. This is how you get the high-value, strategic data about businesses.
Here's a practical example. You certainly want your account to be charged $19.99 when you purchase something for $19.99. At the end of the month, you will look at the aggregate of your purchases and compare it with your pay packet. Do you really worry if saved $200.50 or $205.00? Very few of us will go back and check all the transactions. That we got taxed / or tax refunds to the penny, etc. We are touching the world of statistics and the larger the budgets and spending, the higher is the chance that we made a mistake in particular transactions.
Why is this important? Simply because when you scale your IoT systems, the problem will quickly become one of ensuring a baseline of security, reliability, accuracy. You will never be able to do that on the device level.
That's why I believe that "Secure By Design" will not scale enough to solve the problem of IoT security. It will be management systems to give users confidence in IoT, that will ensure that devices will reliably work and that encryption will enhance the use of IoT, not hinder it. That's what we are doing with KeyChest.
Certificate expiration causes costly downtimes and complete breakdowns of encryption. Our expert service automatically checks and renews your certificates, on time, and correctly, so you can start every day with confidence.
