The State of PKI by AppViewX
AppViewX has conducted a research during the 2019 BlackHat conference asking cybersecurity professionals about their experience with PKI. I will give you an alternative exec summary.
You can find the original report at pages.appviewx.com. Their exec summary highlighted the following three numbers:
- 40% use encryption to protect private keys - now this is something of a problem and you are likely to really encrypt only high-value keys, e.g., private keys of internal certificate authorities. The problems is that many servers only work with text files and can't do decryption.
- 30% of companies use spreadsheets to track their certificates.
- 5% of companies have at least 5 expiration-related incidents every year.
Other Facts
Let's have a look at other information that the report provides, section by section:
- Frequency of outages due to certificates
- Use of best practices
- Business impacts of certificate expiration outages
- Challenges of deploying and managing PKI
- Need of PKI for new disruptive technologies
Certificate Expiration Outages
This is a bit confusing as it doesn't quite support the figure from the exec summary so let's have a look at the detail.
65% experienced 1 to 10 outages - application or device - and an additional 25% of respondents had more than 10 outages. It is in line with a previous study of Venafi from 2017. It is actually 10% more as Venafi found that only 79% of business experience an outages due to an expired certificate.
While not conclusive, it certainly suggests that the problem is getting worse. This is something we can see when talking to companies and we know that the number of certificates grows by 5-10% every year. That means that the number of "near misses" grows and it will eventually lead to downtimes as the statistics can't be fooled forever.

The report further looks at data breaches caused by expired certificates, which stands at 6%. I believe that is a little consolation for companies as they are more concerned about their revenue than a risk of security incidents. Although the general data protection act (GDPR) and the California Consumer Privacy Act (CCPA) have caused internal governance changes in companies.
Best Practices
This section focuses on three aspects: certificate management, private key protection, and monitoring.
I am not quite sure what the private key protection means. The mainstream format to protect private keys is PKCS#12, which is a password-protected file. Linux systems would not use any password once the private key is installed and Windows will allow web servers (IIS) access private keys without passwords as well.
However, protecting keys of certificate authorities is important as their compromise would impact large numbers of servers and services and possibly cause a complete breakdown of the security of internal PKIs and all systems that depend on them.
Certificate management tools are more interesting:
- 20% use certificate lifecycle management tool
- 16% use spreadsheets
- 33% have custom solutions
- 30% have an issuer-provided tool
The two middle numbers are interesting, and especially the high number of companies that built their own custom solution is surprising. The reason being that these tools are unlikely to scale. They also often depend on people who built them and there is a relatively small chance of having a well-documented system that will keep running when the team changes.
Only 39% of companies do monitoring as well as audits of certificates. Let's look at this number and the previous breakdown of management tools. Let's assume that lifecycle management tools provide audit and monitoring.
That leaves 19% of 63% (custom solutions and isssuer-provided tools) include audit and monitoring. That is only one fifth of companies. The rest will do some monitoring or audit, but not both. That is probably the most interesting number so far.
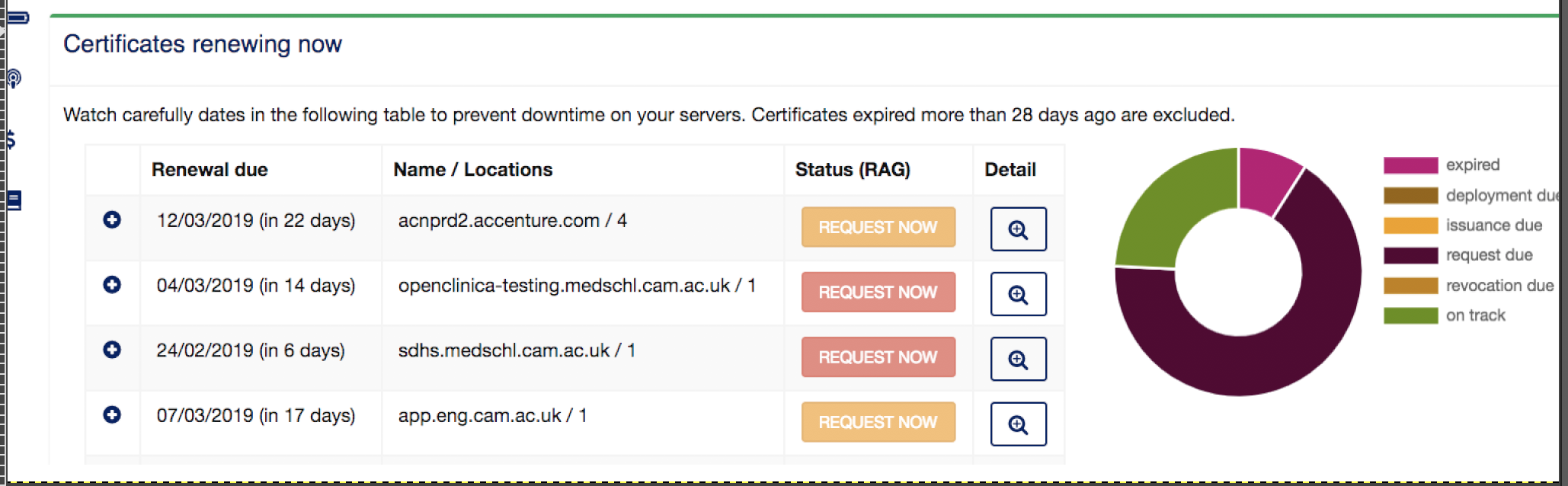
A simple view showing your risk in the next 7 days is the first step for effective certificate management.
Business Impact of Certificate Expiration
The numbers in this part of the report are focused on concerns, not necessarily on the actual history and experience of companies.
A quite non-European number is 40% worried about a potential legal action and fines. It is interesting, because certificates would usually cause downtimes and I'd expect the main impact to be a breach of SLAs or similar.
The two main areas of concern are, however the loss of revenue - 62% - and the loss of productivity - 51%. A quarter of companies also recognized remediation costs as significant. What this means is a tough life for IT managers and system administrators. While they may not necessarily be in a position to improve the management of certificates and internal SSL certificate monitoring, they will be required to restore systems in the shortest possible time 24x7.
The aim of best practices is to minimize the number of near misses and eradicate downtimes. Use of a simple SSL monitor can only get you that far and effective certificate management requires an efficient management of the whole lifecycle.
HTTPS Certificate Cost is a combination of several significant items. The purchase cost of certificates - this item can be lowered by volume purchases or using systems that pass the volume savings to customers. Monitoring and audit cost that would comprise the internal labor costs or the cost of a third-party service, which can be fixed unmetered, or calculated per certificate. The third is the cost of certificate installation, which can be planned and calculated for well-managed certificate inventories. The last one is the hardest to measure as it's based on the probability of incidents. It would involve high levels of stress, a loss of revenue and productivity, brand damage, etc.
Challenges of PKI
Let's start with numbers:
- 74% - lack of visibility
- 46/48% - lack of skills and understanding
- 20% - technology limitations
What's interesting is that there are several free / open-source tools that can help detect certificates and improve the visibility. The matter of fact is that the tools will not provide the regular and up-to-date information you need for confident certificate management.
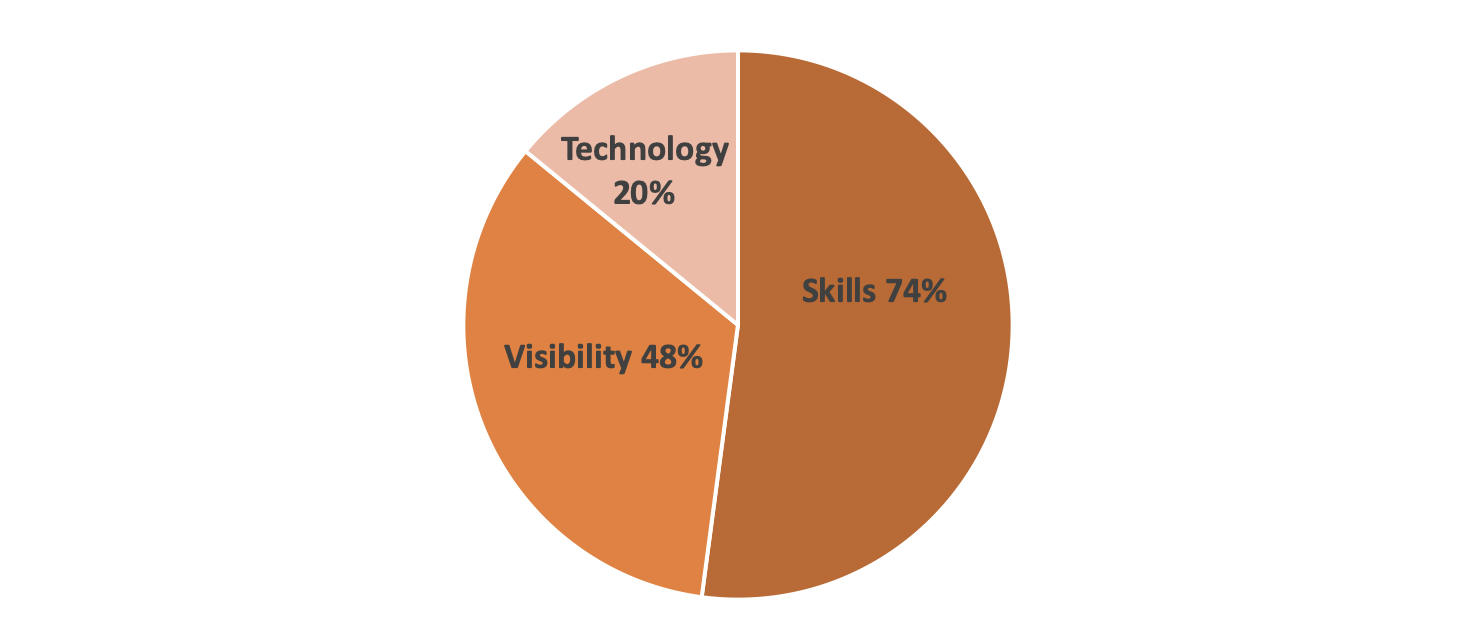
Main challenges of certificate management
New Technologies Require PKI
We can easily skip the "disruptive" from the section title. Where ever you look - from RESTful APIs to mobile web (AMP) to building information-rich online presentations, you need SSL/TLS and you need certificates.
Even small businesses have to tackle the PKI management problems that were experienced only by corporations 5 or 10 years ago. Even when you just want to run a more traditional online business, you need to include the cost of HTTPS and certificates in your budget. It can be a direct cost or increases in the service cost of your managed service providers. While 60% of companies said that the next big trend was IoT, 50% mentioned "cloud". And the cloud is what any business with online presence needs today.
When one certificate expires, there would be 10, 20 or more certificates that "almost expired" and there may be a hundred others that may expire in the next week or two. The problem of certificate management is its scale. The scale that only grows.
