KEYCHEST - Confidence In Your Online Business
While KEYCHEST as a brand started as a straightforward expiry management service for Let's Encrypt, it has become a service with a rich set of features and there is still several technologies that wait for production deployment.
The ultimate goal of KEYCHEST is to give you the confidence that your online business keeps running without interruptions. While you can create a new website in minutes, its online visibility now depends on a huge number of technologies depending on automations. If any of them fails, it has a direct impact on your business.
KEYCHEST will give you advance warnings when your automated processes fail well before they can impact your business. It will let you know when you reach the limits of technology. The limits that you should never worry about nor understand. Whether its rate limits of Let's Encrypt certification authority, temporary network failures, changes in web browsers, data caching. We use a range of technologies to provide this confidence in a form of an unmetered service for a fixed monthly or annual cost.
Some call it PKI (public key infrastructure), what we offer is much more - it's automated management of your web security and PKI is just a small part of what powers KEYCHEST. We believe web security should be a simple service that just works - like a network to connect you with your customers, a database to store your data, or a payment service that securely collects payments for your goods.
4% of businesses experienced more than 100 outages in a year due to expired web or internal services, while 79% of businesses experience at least one outage in a year. (Venafi market research).
The KEYCHEST architecture integrates several cutting-edge technological innovations developed by a team of academic researchers and experienced security professionals. These technologies tackle the core issues that determine a successful automation of key management. This enables KEYCHEST to integrate existing key management products into a scalable service. But ultimately, to give you the confidence that the web security keeps powering your business, not taking it down.
KeyChest can be the gatekeeper for all your certificate management
KEYCHEST own technologies include:
- CloudFoxy - secure hardware “virtualization” platform providing access to large numbers of high-security chips. There is a specific level achieved in independent security evaluations - FIPS140-2 Level 4 for physical security. This level of security is quite unique, but we can offer this in the form of a cloud service;
- PKI and encryption service for high-security chips - it's a bit of a mouthful, but this provides one crucial service - cloud-friendly encryption management with enrollment automation;
- Instant PKI – root CAs and PKI instances with FIPS140-2 L3 compliant key storage – legacy (PrimeKey/EJBCA), as well as modern products (e.g., HashiCorp Vault), we try to diverge from legacy PKI systems that are clunky, difficult to setup and manage but they will be used for quite some time due to internal dependencies;
- KEYCHEST Expiry Management Service – a cloud management service with a global database of all public certificates with instant search. It is also the integration framework for all other technologies that your business may need. From an ssl expiry check, a web domain expiration audit, to real-time updates.
Technology Means Little - What You Really Need is The Confidence in Your Business Uptime
This post is an overview of our technology that provides everything you may need: renewal of certificates, one view with all incidents, management support for products you may use to manage your certificates, a detail information for a given endpoint (ssl expiry check, configuration reports, continuous monitoring) as the big picture of your whole business.
All that will only help your business if it can ensure that it keeps an eye on every part of your online business. And that's what KeyChest does - it finds any new parts of your secure business configuration on its own. You simply can't forget to manage your new service - we add it automatically. The reason is because we want to give you the confidence in your computers, networks, and services.
Global Certificate Database
We built our own global database of internet certificates issued over the last several years. It currently contains almost 10,000,000,000 entries (early Feb 2020) and provides instant search for domains and subdomains. The database itself will add new certificates in as little as 20 seconds of their creation. This provides KEYCHEST with a global view of internet encryption that can be used e.g. to identify phishing attacks using similar domains, growth of company infrastructures, quality of encryption management, and so on.
CloudFoxy
While a hardware platform, it truly virtualizes secure chips for high-security applications. It can provide up to 600 secure chips for high-value keys in one server, accessible with modern web APIs. It’s versatile design can be used for multi-party signing or encryption, which we demonstrated with UCL London at the BlackHat and DEFCON in 2017.
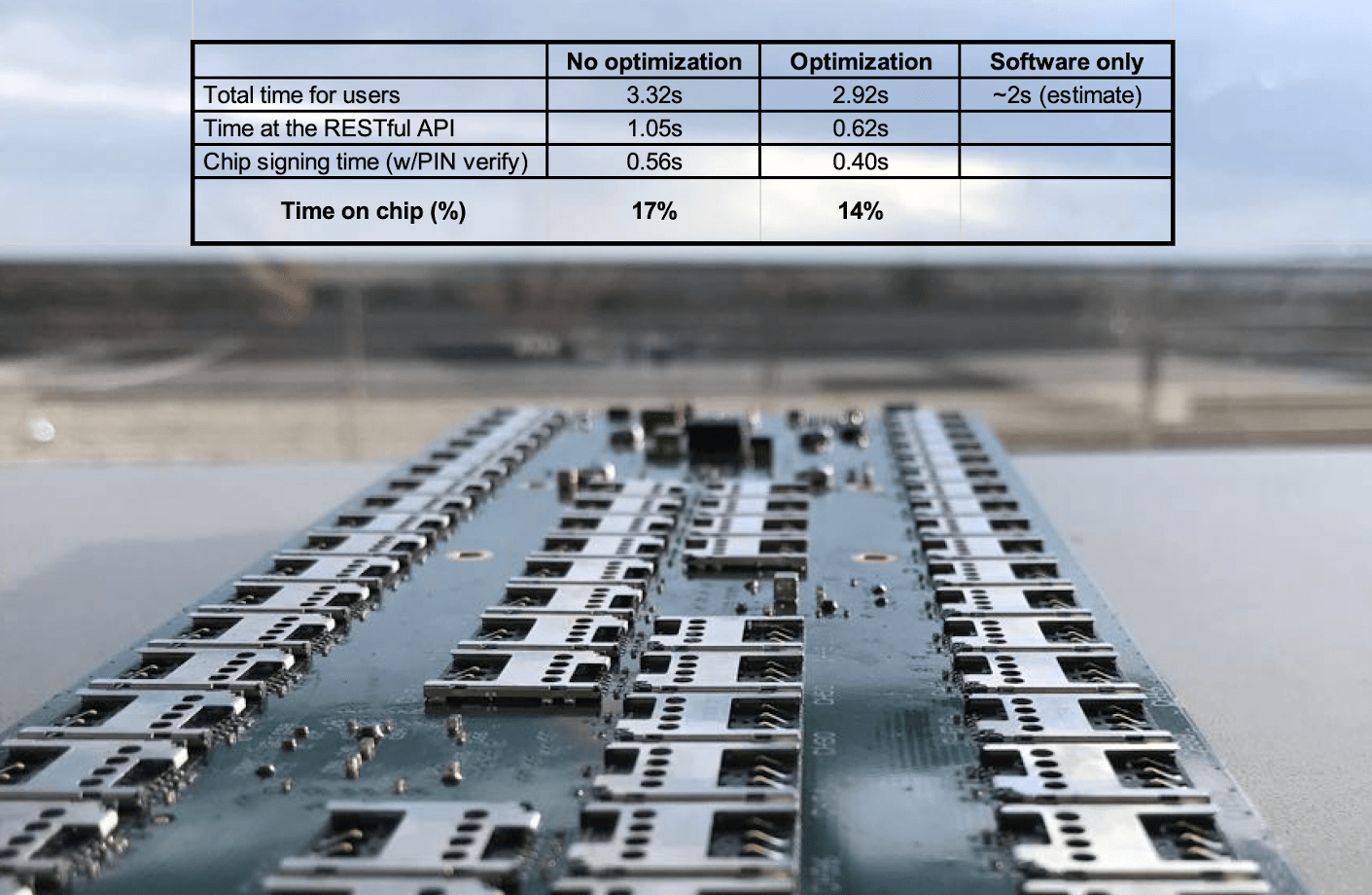
CloudFoxy is a versatile security platform suitable for root CAs as well as high-security (e.g., eIDAS) document signing. Timing figures for for eIDAS signing, including PIN validation).
“Full-stack” PKI integrated service – demonstrated on Amazon AWS, allows launching new PKI systems with FIPS140-2 Level 3 hardware in a fully automated fashion.
KeyChest service
It's the main integration service for all other technologies. Its automatic, continuous discovery of new certificates makes it an ideal tool for internal and external audits in small enterprise environments. You don't have to install a single piece of software to manage your web security and we offer lightweight software agents with a granular access control you can enforce internally.
KeyChest now integrates renewal automation with third-party trust providers Thawte, Symantec, GeoTrust, COMODO and SectiGo via APIs.
