HTTPS Certificates - Keys and Issuers
Let's have a look at the quality of keys in internet certificates and who are the main certificate issuers.
This time, I have analyzed a sample of 500,000 certificates from the database of KeyChest. I have looked at the numbers of all certificates that KeyChest pulls from CT (certificate transparency) logs and also at data of server audits. The two datasets differ as we request more certificate than we actually use – especially when they are free. When I query our CT (certificate transparency) database directly, I can see large numbers of duplicates, but it’s non-trivial to eliminate the effect of CDNs (content delivery networks). The data from actual audits of web services show how important this aspect is.
Anyway, I had worked for large enterprises and I was curious. An enterprise is still unlikely to use Let’s Encrypt but how successful are “enterprise trusted” names elsewhere. And it’s pretty bad for some names I believed to be market leaders.
Let me start with some simple but nevertheless interesting stats around algorithms and key length. The data is for domains audited by KeyChest.
Algorithms and key length
- 12% RSA 4,096 bits
- 68% RSA 2,048 bits
- 2% RSA 1,024 bits
- 15% ECC 256bits
- 0.8% ECC 384bits
Personally, I’m surprised by the large use of elliptic curve (ECC) certificates, which I’d expect to be less than 5%. So well done to all the admins who optimize their servers for faster encryption.
Types of certificates
- 1.2% - self-signed certificates
- 4.8% - extended validation certificates (EV)
- 20.5% - organization validation certificates (OV)
- 73% - domain validation certificates (DV)
Another two statistics I was interested in was CDN and wildcard certificates:
- Cloudflare certificates: 15%
- Wildcard certificates: 22%
What you can start seeing from this is the role of CDNs, and especially Cloudflare among KeyChest users. Cloudflare would have OV certificates, which means that when we take those away, only organizations are more likely to use the most expensive EV certificates than OV certificates.
You’ve got better things to do than worry about web certificates. Leave them to KeyChest.
I’m finally getting to the results of the main excercise – how big is Let’s Encrypt. It is not 80% but it’s still majority of all certificates that KeyChest pulled from CT logs.
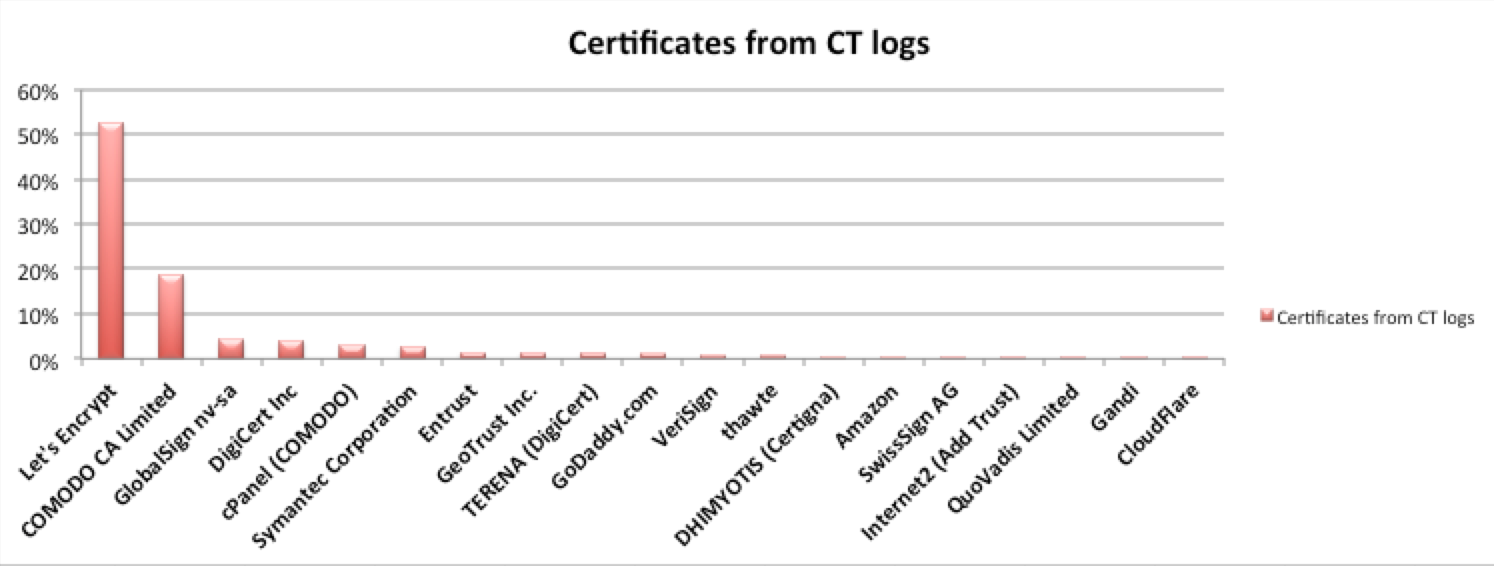
Distribution of certificates per issuer
There are some unexpected entries there (cPanel) but in general – there are basically 2 leaders in the market – Let’s Encrypt for free, short term certificates that we are using on our web servers. COMODO used by main CDNs. GlobalSign and Digicert are sharing the market of “end user organizations” with COMODO.
Let’s have a look at the data from actual audits of servers. I have done two samples, one for audits over the KeyChest lifetime (since Q3 2017) and a sample of audits executed in Q1/2019.
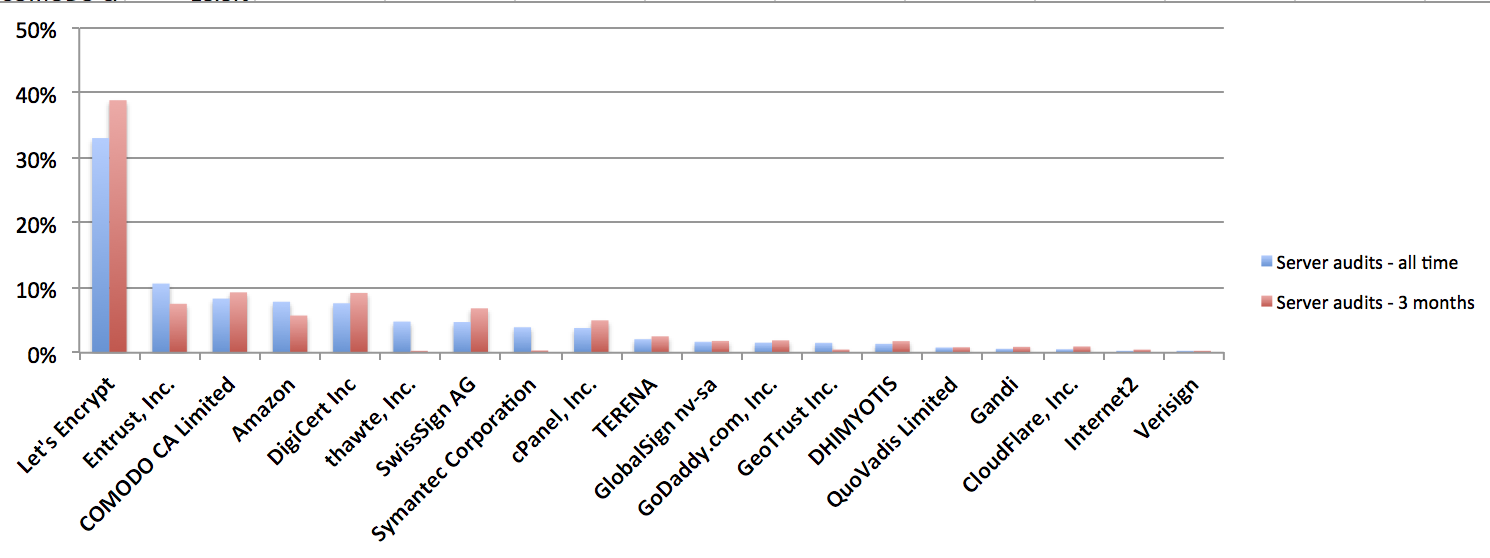
Distribution of certificates from server audits.
The main number here is the increase of Let’s Encrypt – from 33.1% to 38.8%. Another interesting point is that COMODO is back in line with other commercial issuers – something that most likely reflects how CDNs use certificates. My experience is that the number of certificates issued for CDNs is much higher than what can be see on CDN servers (although we are limited by the use of only a couple of DNS servers we use to resolve domain names to IP addresses).
You are overwhelmed with certificates to manage, websites are regularly going down, and your stress spills over into your personal life. Let KeyChest get you back on top.
Some interesting numbers. Certainly well done to Let’s Encrypt, which seems to keep getting new customers as the long-validity certificates expire. I was surprise by the amount of certs issued by COMODO. It seems they benefit from their targeting of CDNs, as well as low cost for small users.
