Malware Cerberus: For Hire to Steal Google 2FA
A new version of the "Cerberus" Android banking trojan will be able to steal one-time codes generated by the Google Authenticator app and bypass 2FA-protected accounts.
ZDNet reports: “Google launched Authenticator as an alternative to SMS-based one-time passcodes. Because Google Authenticator codes are generated on a user's smartphone and never travel through insecure mobile networks, online accounts who use Authenticator codes as 2FA layers are considered more secure than those protected by SMS-based codes.”
Let’s step back. The attack techniques Cerberus are nothing new. The crucial one is the “overlay” technique when the malware captures information from touch screens. What makes Cerberus dangerous is a mix of three things: it’s a completely new code, privately used for 2 years without detection, publicly advertised as malware for hire.
Other sources:
- Report: new Android malware can steal 2FA codes from Google Authenticator
- Advanced Malware for Android can steal PINs, patterns, and 2FA Codes
Cerberus Trojan - Summary
Summary of highlights as reported by ThreatFabric:
- Private use: from 2017
- Identified: June 2019
- Code: written from scratch - unusual, hard detection
- Origin: known, official Twitter account, openly ridicule AV community by demonstrating shortcomings
- Monetization: renting
- Contact: Twitter @androidcerberus
- How it works: requests a set of privileges, privilege escalation to gain the required level, overlay, remote management
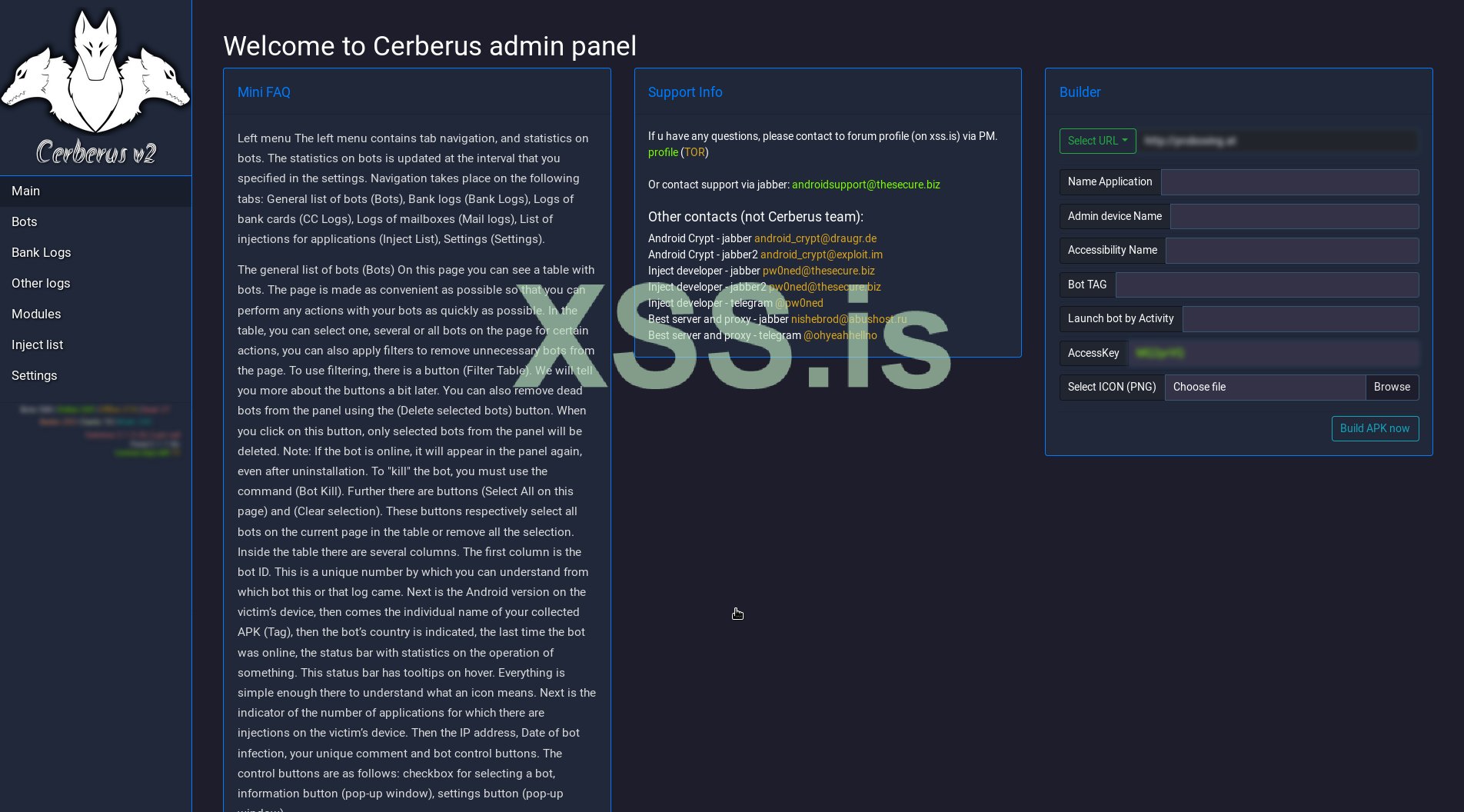
Cerberus CC / admin panel - source: Twitte @androidcerberus
Google Authenticator Threat
It has not been seen in the wild yet and it’s not clear whether or when it will be available, but the threat is plausible.
The attack uses a common overlay feature when the malware creates a transparent clock between the touchscreen and the active application. You can imagine it like music playing in the background when you read your favorite subreddits. Instead of using the Android speaker in the background, it uses the screen in an “invisible foreground” or a visible, faked copy of the original app/webpage.
What is Google 2FA Authenticator
To use Authenticator, the app is first installed on a smartphone. It must be set up for each site with which it is to be used: the site provides a shared secret key to the user over a secure channel, to be stored in the Authenticator app.
Once installed, users have to select the website or application where they need to login. The Authenticator will then create a unique 6 digit code that can be used only once and/or for a short period of time, e.g., 5 minutes.
Google Authenticator is the most popular 2FA app that implements two-step verification services using the Time-based One-time Password Algorithm (TOTP; specified in RFC 6238) and HMAC-based One-time Password algorithm (HOTP; specified in RFC 4226), for authenticating users to websites and applications.
Origins of Banking Trojans - Gustuff
Gustuff was identified in 2016 and has been continuously upgraded and enhanced. (Which is something that justifies the fun that @androidcerberos are making of the AV community.) It has been sufficiently successful to get major changes in its architecture and expansion of its feature set. It was the first beast that used Android Accessibility Service to improve its stealthiness via remote management (RAT).
Given how much we rely on antivirus software, here’s some food for thought. After 3 successful years in the wild, the actors started developing a new version that “slowly phased out” the original version. This process took several weeks and resulted in a complete replacement of Gustuff with a new version.
The new version added some new features such as keylogging, browser overlays and even an ATS (Automated Transaction System) on top of the RAT.
KeyChest manages your SSL for you. Set up our cloud service and then forget it. Restore confidence in your IT and make encryption a valuable business asset instead of a time-sucking drag.
Check the status of your web domain with our instant online domain audit tool.

